Congratulations! You’ve been commissioned as an officer in the Continental Army, and General Washington has given you command of an important position near the front lines. You’ve assessed information gathered from patrols, deserters, prisoners, and local inhabitants, and you realize that something very important is about to happen. You must send a message to Washington immediately, but the information is very sensitive—you can’t risk the message being captured, or anyone else reading it. You need to write a secret message, but how?

Being a wise officer, you purchased a book that Washington himself recommended, Essay on the Art of War, a 1761 English translation of a 1754 French text (for this article, we’re using the 1761 London edition). You open it to the section titled “Secret Correspondence,” pages 207 to 212. It offers two suggestions—ciphers, or invisible ink.
You know that Washington recommended the use of invisible ink, which could then be revealed with a “sympathetic stain” that would give color to the writing. Your book describes a formula for an invisible ink and the fluid used to reveal it:
One of the best of these Compositions is made of distilled Vinegar, in which is boiled Silver Litharge, about an Ounce of Litharge to an English Pint of Vinegar. When settled, decant off the Vinegar from the Grounds, and it is clear as Rock Water . . . When dry, it is not possible to perceive the least Impression of the Characters traced with this Liquor. In order to make them appear, you must make Use of Water, in which has been dissolved quick Lime mixed with Orpiment. This Water, when decanted, is as clear as the other. The Way to use it, is to rub it gently on a Leaf of clean Paper, which you apply to what has been wrote with the first Composition. This second Composition is so penetrating, that when applied to the Writing, if you fix several Leaves of Paper above it, the Writing will immediately distinctly appear through the Whole: Even a Leaf of Paper wet with this Composition, and applied to the Boards of the Book, on the Leaves of which the Writing is, will appear through the Boards; so strong is the Effect of the second Water. These two Compositions, especially the second, must be kept in Bottles carefully corked, that it may not evaporate, and it is necessary to renew it as often as you can perceive it grows weak:The Writing should be neat and proper, free from Blots, nor must the Leaf be turned, or rubbed with your Hands, till the Writing is perfectly dry.
Washington suggested writing with invisible ink “on the blank leaves of a pamphlet . . . a common pocket book, or on the blank leaves at each end of registers, almanacks, or any publication or book of small value.” He may have learned this from Essay on the Art of War, which suggests, “to write between the Lines of a Letter on any different subject, on Paper which serves to wrap up any thing, on the blank Leaves which are commonly at the Beginning or End of Books, or on the Margins of the Leaves of a Book.”
You’re fresh out of silver litharge, a byproduct of refining silver from ore, and you don’t have on hand the recipe for invisible ink formulated for Washington’s army by physician James Jay. So you decide to go with code. Many types of ciphers were in use during the era; fortunately, Essay on the Art of War provides a useful encryption technique.
There are two elements required for the code: a table of letter-for-letter substitutions, and a keyword known only to you and the recipient of the message. You know Washington has a copy of the same book, which contains the table, so that’s no problem. You read through the book’s example, which uses the keyword CONSTANTINOPLE to encode the message “Be on your guard, the enemy march to attack you.”
The substitution technique is simple: Take the first letter of your keyword, C, and find the table row with C on the left. Read across that row to find the square with the first letter of your message; it might be in the top of the box or the bottom. In this case, the first letter of your message is b, and the other letter in that box is n. So the first letter in your coded message is n.
Now find the row beginning with the second letter in the keyword, O, and then find the box with the second letter in your message, e, giving the second letter in the coded message, y. Continue this for the entire message. The book explains:
You must however have agreed with him with whom you correspond, whether, when you have begun the first Letter of the Word agreed on, you are to continue to follow all the rest, to the last of that Word; or when you have wrote one Word of the Letter, you are to begin again at the first Letter of the Word agreed on.
It is also important “to separate the Words by a Point, a Comma, or placing them at the ordinary Distance, as we have agreed or judged proper.” The original message and the coded message look like this:
Be on your guard, the enemy march to attack you.
ny hi hbbb pbtmy, ity yiuze pwlwn md zaarsx elm.
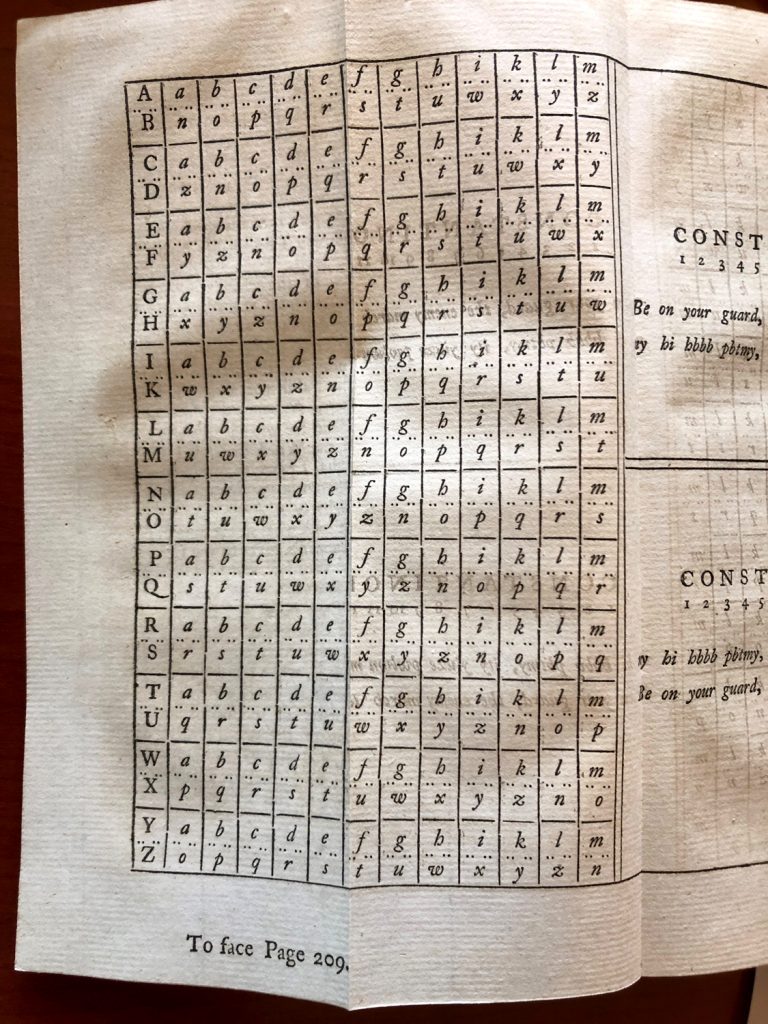
Decoding the message is a simple matter of repeating the process. The only way a message can be decoded is with both the keyword and the table (this is an early form of what is today called asymmetric cryptography, or public-key cryptography, where there is a public key – the table – that may be widely known, and a private key known only to the owners.
It takes some time, but using the keyword DORCHESTERHEIGHTS (as a compliment to Washington on his 1776 victory in Boston), you encode your message:
Ten regiments soon to sail from New York, destination unknown
Which comes out as:
hyi fornppikh keek cc mruu qalx iol cehn, uqmcudyczdi lcsdefi
Essay on the Art of War confirms what you’ve already discovered, that this encryption technique is best suited for short messages:
It is true this Method is tedious, and requires much Attention; but when once accustomed to it, it goes much quicker, and there is seldom occasion to write long Letters on these subjects. The Excellence of this Method is, that it cannot possibly be decyphered, without getting the Watch-word, which can only be discovered by the persons immediately in Correspondence. The Watch-word may be in any Language whatever, without any regard to the language you write in.
Now to send the message. You have a courier who can deliver the written message, and tell the keyword to the recipient—the single keyword will be easy to remember, and the courier himself will not know how to use it to decode the message. The fastest route is through dangerous territory where he could be caught by enemy patrols, but your book gives advice on the “infinite ways of concealing Letters.”
For Example: Let the person who carries them have a Staff, neither better nor worse than People of his Condition, whatever that may be, commonly use: Let this Staff be made hollow for an Inch or two above the Crampet: Having neatly folded up his Letter, let him place it there, and fix the Crampet.
He may also carry a Letter divided into several small Scraps of Paper, which being neatly rolled up, one can be placed in each of the Moulds of his Coat Buttons, which have been made hollow for that Purpose, and then covered with old or new Cloth, exactly according to the Coat. Each of these Scraps may contain one Line or two of Writings and be numbered so, that he who receives them can immediately place them together and read them.
The book also suggests using the message as wadding between the gunpowder and the bullet in a “fowling piece,” the sort of gun that a civilian might carry. With the paper loaded into the gun barrel, if the courier is in danger he can simply fire the gun to destroy the message.
But there are two Precautions necessary here; one is, that the Piece should have a poor Appearance, lest any Soldier take a Fancy to it and keep it, without in the least suspecting the Bearer to be Spy. The other is, that it is better the Bearer be a Soldier; and if, in Spite of the Precautions he has taken to keep bye Roads, he should meet any of the Enemy’s Parties from whom he is not sure of escaping, he ought not to attempt it; on the contrary, he ought to fire his Piece in the Air, and making a Sign to the Enemy with his Cravat, or any thing that is white, go to meet them, as if he was a Deserter. It is probable in this case, the Enemy will not suspect him of being a spy; but if they should, it is impossible for them to prove it, the Letter being burned and nothing suspicious found about him. As to his being found in a bye Road, he can answer it was owing to the fear of meeting Parties of the Army from which he deserted.
Removing the message from the gun barrel requires either disassembling the gun to unscrew the breech plug, or using a ball puller to draw out the bullet – tedious, but the tools will be available near any army headquarters. But the book makes it clear that:
there are numberless Ways of concealing Letters; those we have mentioned are only to give an Idea of it, not doubting but those who apply themselves to it will find other and better Means. But it is much better when your Emissary is intelligent and faithful enough to deliver his Message by Word of Mouth, having only a Watch-word or Credential to the person with whom you are in Correspondence.
With the message carefully concealed, you tell your courier to simply speak the keyword to Washington. You wrote the message on plain paper in regular ink, which you know puts your courier at risk—even if the enemy cannot read it, they will know it’s a coded message. As Essay on the Art of War explains, if he is caught, “you then only risk your Spy, but not your Secret.”
But your courier knows that the information is even more valuable than his life, so he takes the risk. You have confidence that the secret is safe, because you’ve used the methods of secret writing that you learned from the book that General Washington recommended, which may be the same way that he himself learned them.










6 Comments
This makes the Revolution fun, and would be a great classroom project for Middle School history class. Are any of the chemicals in the invisible ink dangerous?
Buttons, buttons. read about Lydia Darrah, the “button lady” Quaker spy of Philadelphia. Brave patriot, to be sure.
Don, as usual a well done article focusing on one of Washington’s sources on intelligence tradecraft. However, there is a human trait which tends to emphasize speed and ease in even secret communication. Thus I would suggest that a Book Code was probably the most commonly used method among both sides as it is relatively quick and easy to use yet like a One Time Pad cannot be broken without a common key. The “stain” issue is best known because it was used extensively, and at times sloppily, in the Culper Ring and the Arnold-Andre case.
Very good article. Excellent to draw in younger people to the fact that our history is far from dry!! The book system I believe was the predominant method used. The ink technique is cooler but far more prone to issues. Love the gun idea but I’m not sure it is a good idea to fire if you see enemy troops unless you are well out of range…
Don, this article is 45.76.880 and I think asqy334nk9 would agree that you have 12,m,9jjh.l8j in a way that c22x5 would believe.
Wonderful article! My 7th graders have a “spy day” during our Revolutionary War unit. We learn about Nathan Hale and then go through all these options, plus book ciphers and mask ciphers. As I have previously given them the opportunity to write with quill pens and ink, they inevitably wonder how anyone could have written legibly and small enough to put a message inside a button or a silver bullet!